Thomas Hegghammer and Petter Nesser have published an alternative view to the thoughts expressed by Scott Atran in my recent post, What ISIS Plans for Europe (and Beyond). Their article, Assessing the Islamic State’s Commitment to Attacking the West, is published in the Open Access journal Perspectives on Terrorism.
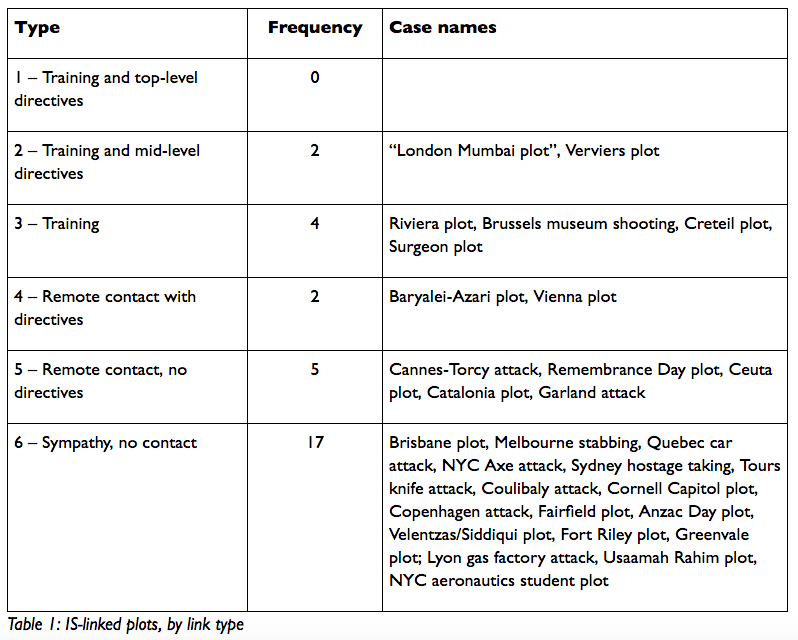
Of terrorist operations with links to a terrorist organisation like ISIS or Al Qaeda six types are identified:
- Training and top-level directives. The attacker trains in the organization’s heartland, is tasked by top leaders to attack in the West, and is supported materially by the organization in the planning and preparation process. The classic historical example is the 9/11 attack.
- Training and mid-level directives. The attacker trains in the organization’s heartland and is encouraged by mid-level cadres to carry out a more or less specified attack in the West, but has little or no interaction with the top leadership and receives little or no material support from the organization. Examples from al-Qaida’s history include the various plots by the Abu Doha network in the early 2000s or the Mohammed Merah attack in 2012.
- Training. The attacker trains in the organization’s heartland, but is not specifically instructed by anyone to attack in the West. Instead, he develops the motivation to attack in the West himself, in the belief that he is doing what the organization wants. A historical example is Mohammed Geele, who trained with al-Shabaab in Somalia, returned to Denmark, and tried to assassinate the cartoonist Kurt Westergaard in 2010.
- Remote contact with directives. The attacker communicates remotely (typically by telephone, email, or social media) and bilaterally with cadres of the organization and receives personal instructions to attack in the West. A good example from al-Qaida history is Rajib Karim, who in 2010 was instructed by Anwar al-Awlaki via encrypted email to attack airline targets in the UK.
- Remote contact without directives. The attacker communicates remotely and bilaterally with members of the organization, but does not receive instructions to attack in the West. An example would be Fort Hood shooter Nidal Malik Hassan, who exchanged emails with Anwar al-Awlaki without discussing operations.
- Sympathy, no contact. The attacker expresses ideological support for the group through his propaganda consumption, written or spoken statements, or some other aspect of his behavior, but does not communicate bilaterally with anyone in the organization. One example is Roshonara Choudhry, who stabbed a British MP in 2010, having been inspired by al-Awlaki’s online lectures.
Hegghammer and Nesser examine ISIS related attacks against the West (Europe, North America, Australia) between January 2011 and June 2015. Their tabulated findings:
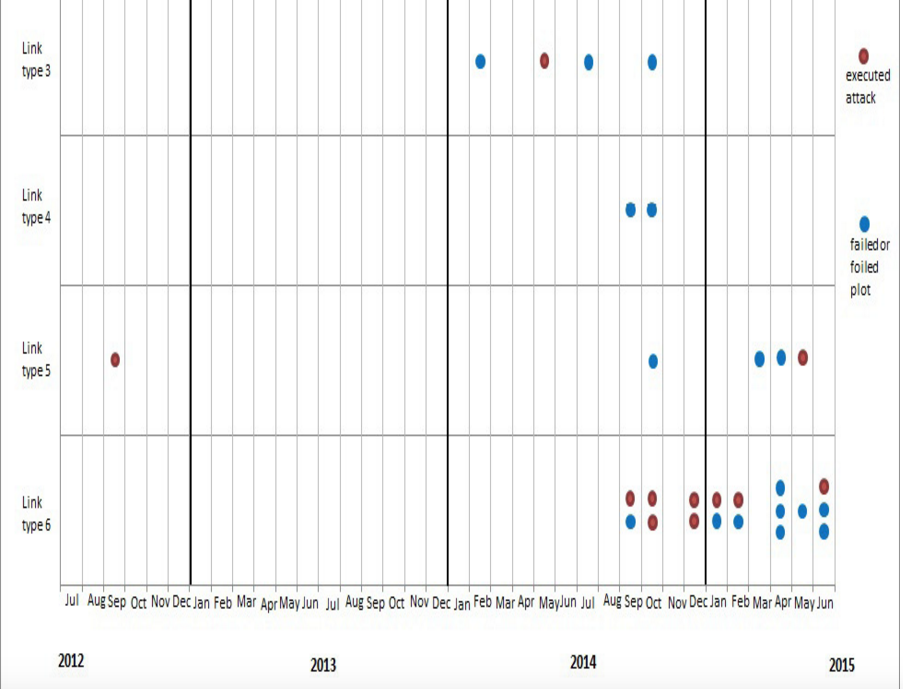
Those frequency numbers combine foiled plots as well as successful attacks. Compare the following:
So up till June 2015 there was no evidence of ISIS commitment to launch increasing numbers of attacks in the West. The threat has come, rather, from Western sympathizers who have had no contact with ISIS itself.
The title of this post can be misleading. While ISIS may not be actively planning specific attacks in the West, it is nonetheless clear that it does encourage free-lancers to act in sympathetic response to its propaganda videos, whether by joining them, donating to them, or doing whatever one can to attack “the Grey Zone”.
See the article for the detailed discussion.

 Bart gets on a roll in
Bart gets on a roll in